Today’s digital landscape is full of ever-evolving cyber threats. Securing your organization’s identities has become very important. Azure Identity Protection is a strong ally. It empowers you to strengthen your defenses and protect your most valuable assets: your users’ identities. This strong security service gives you a single view of potential weaknesses. It also gives you the tools to stop risks and react fast to incidents.
Unveiling the Essence of Azure Identity Protection
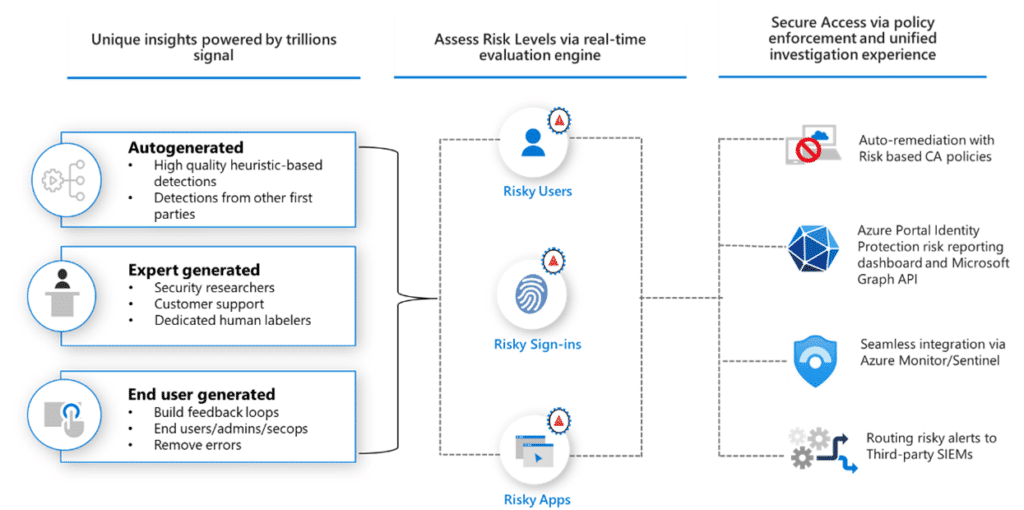
Azure Identity Protection is an intelligent security solution that leverages adaptive machine-learning algorithms to detect anomalies and suspicious activities associated with user identities. By continuously monitoring and analyzing user behavior patterns, sign-in locations, device health, and other contextual factors, it can identify potential threats such as leaked credentials, compromised accounts, and impossible travel scenarios.
The service generates comprehensive reports and alerts, enabling administrators to investigate and respond promptly to potential vulnerabilities. Moreover, Azure Identity Protection offers powerful remediation capabilities, including enforcing multi-factor authentication (MFA) and facilitating secure password resets, ensuring that issues are swiftly resolved and risks are mitigated.
Reaping the Benefits
Implementing Azure Identity Protection within your organization yields numerous advantages, fortifying your security posture while streamlining operational processes:
- Proactive Threat Detection. By harnessing the power of machine learning, Azure Identity Protection can identify potential threats before they escalate, enabling you to take preemptive measures and minimize the impact of security incidents.
- Reduced Account Takeover Risks. With its ability to detect compromised accounts and risky sign-in attempts, Azure Identity Protection significantly reduces the risk of account takeovers, safeguarding your organization’s sensitive data and resources.
- Rapid Incident Response. By providing detailed insights into risky users and sign-in activities, Azure Identity Protection empowers your security teams to investigate and respond to incidents promptly, minimizing potential damage and ensuring business continuity.
- Enforced Multi-Factor Authentication. Azure Identity Protection allows you to implement risk-based conditional access policies, automatically enforcing MFA for high-risk scenarios, adding an extra layer of security to your authentication processes.
- Streamlined Identity and Access Management (IAM). With its integration into the Azure Active Directory (Azure AD) ecosystem, Azure Identity Protection seamlessly aligns with your existing IAM policies and procedures, ensuring a cohesive and efficient security strategy.
- Improved Visibility and Reporting. The comprehensive reporting capabilities of Azure Identity Protection provide you with detailed insights into your organization’s identity-related risks, enabling data-driven decision-making and facilitating compliance with industry regulations.
Maximizing the Value in 8 Steps: Best Practices for Azure Identity Protection
To fully harness the potential of Azure Identity Protection and ensure its effective implementation within your organization, adhering to industry-recognized best practices is crucial. By following these guidelines, you can optimize your security posture, minimize risks, and maximize the return on your investment.
1. Engage Stakeholders Early and Effectively
Securing buy-in and aligning expectations with internal stakeholders, such as IT security teams, infrastructure/operations teams, application owners, and business leaders, is essential for smooth adoption and optimal utilization of Azure Identity Protection. By engaging stakeholders early in the process, you can ensure a shared understanding of the solution’s capabilities, define roles and responsibilities, and gather valuable insights tailored to your organization’s unique needs.
To achieve this, consider the following steps:
- Identify all stakeholders impacted by Azure Identity Protection, including security administrators, IT teams managing authentication systems, application owners, helpdesk personnel, and end-users.
- Conduct workshops and demonstrations to showcase Azure Identity Protection’s capabilities, such as risk modeling, automated response mechanisms, and reporting features.
- Define clear roles and responsibilities for each stakeholder group in deploying, supporting, and extracting value from the solution.
- Gather input from stakeholders regarding desired policies, alert configurations, and integrations with other tools like Security Information and Event Management (SIEM) solutions.
- Establish an onboarding plan for end-users impacted by MFA registration and risk-based policies, ensuring a smooth transition and minimizing disruptions.
- Implement a support and escalation process to address issues faced by users during the adoption phase.
- Foster a feedback loop for continuous improvement, allowing stakeholders to provide insights and suggestions for optimizing the solution’s implementation post-rollout.
2. Configure Risk Policies with Precision
Azure Identity Protection empowers you to create Conditional Access policies that automatically respond to user and sign-in risks detected through its AI-driven risk modeling. Properly configured risk policies act as automated sentinels, promptly responding to abnormal activities before incidents occur, thereby minimizing potential threats and ensuring business continuity.
To optimize your risk policies, consider the following recommendations:
- Enable the user risk policy to enforce actions such as MFA or password changes for users identified as high-risk.
- Implement the sign-in risk policy to trigger MFA prompts or block access for risky sign-in attempts.
- Set appropriate thresholds for user and sign-in risks based on your organization’s security posture and risk tolerance. More aggressive thresholds may lead to an increased number of false positives.
- Scope policies to cover all users or specific critical groups, such as administrators, based on your desired level of coverage.
- Exclude emergency access accounts from risk policies to prevent accidental lockouts and maintain administrative access in critical scenarios.
- Leverage the report-only mode to evaluate the potential impact of your policies before full enforcement, allowing you to make informed adjustments.
- Regularly review automated remediations in usage reports to correlate risk detections with user and sign-in actions taken, ensuring the effectiveness of your policies.
- Periodically adjust policies based on an analysis of risk patterns within your environment, ensuring they remain aligned with evolving threats and organizational needs.
- Export risk detections to your SIEM solution for further correlation and enhanced monitoring coverage.
- Conduct thorough testing to strike a balance between robust security measures and a seamless user experience.
3. Mandate Multi-Factor Authentication (MFA) Registration
The Azure Identity Protection policy for MFA registration prompts users to enroll in Azure AD Multi-Factor Authentication (MFA) during sign-in, strengthening account security beyond relying solely on passwords. By enforcing MFA registration, you can significantly reduce the risk of unauthorized access and account compromises, enhancing the overall security posture of your organization.
To effectively implement MFA registration, consider the following best practices:
- Enable policies for cloud services, applications, and systems, and enforce registration for all users. Alternatively, you can opt for a gradual rollout to minimize disruptions and ensure a smooth transition.
- Educate users on the importance of MFA and how it safeguards their accounts from unauthorized access, fostering a security-conscious culture within your organization.
- Provide clear instructions and guidance to users on enrolling their devices for MFA, ensuring a seamless registration process.
- For mobile devices, ensure users have downloaded and activated the Microsoft Authenticator app, enabling them to leverage its secure authentication capabilities.
- For desktops and laptops, guide users to enable phone-based MFA or FIDO2 security keys as their secondary authentication factor.
- Encourage users to register multiple verification methods as backups, ensuring uninterrupted access in case one method becomes unavailable.
- Prioritize MFA registration for privileged accounts, such as administrators, to protect critical access and minimize the risk of unauthorized administrative actions.
- Consider excluding break-glass accounts from MFA enforcement to prevent inadvertent lockouts and maintain emergency administrative access.
- Utilize the report-only mode initially to gauge the potential impact of MFA registration before enforcing it across your organization.
- Evaluate if existing MFA solutions need to be phased out after the successful rollout of Azure AD MFA, consolidating your authentication mechanisms for improved efficiency and management.
- Monitor registration status and follow up with users who fail to complete the registration process after receiving prompts, ensuring organization-wide compliance.
4. Establish Emergency Access Procedures
When configuring Azure Identity Protection risk policies for user and sign-in risks, excluding emergency access or break-glass administrator accounts from the scope is crucial. This precautionary measure ensures that you maintain administrative access to Azure AD in worst-case scenarios, such as mass user lockouts due to policy misconfiguration or synchronization errors.
To establish a robust emergency access procedure, consider the following steps:
- Create at least two emergency access accounts within your Azure AD tenant, ensuring they are granted global administrator privileges.
- Explicitly exclude these accounts from Conditional Access policies enforcing MFA, password resets, or other risk-based actions for risky users or sign-ins.
- Implement a documented process for securing and managing these emergency accounts, including:
- Ensuring that the account credentials are known only to designated individuals, such as Chief Information Security Officers (CISOs) or security leads.
- Rotating the credentials periodically, ideally every 30 to 90 days, to mitigate the risk of unauthorized access.
- Monitoring the accounts for any anomalous sign-in or usage patterns that may indicate potential compromise.
- Outlining a verification process to be followed before utilizing these accounts, ensuring proper authorization and minimizing the risk of misuse.
5. Optimize Risk Modeling with Trusted Locations
Configuring named locations for office networks and Virtual Private Network (VPN) ranges is an essential optimization for Azure Identity Protection’s risk modeling. By declaring internal networks as trusted or known locations, sign-ins originating from these sources will be assigned lower risk scores within Identity Protection. This approach minimizes false positives and unnecessary challenges for users accessing resources from within the corporate network, enhancing the overall user experience while maintaining a robust security posture.
To optimize risk modeling with trusted locations, consider the following steps:
- Create named locations in Azure AD Conditional Access, representing your organization’s office IP ranges and VPN connections.
- Mark on-premises office networks as ‘trusted locations’ once configured, ensuring that sign-ins from these locations are treated as low-risk.
- Configure VPN IP ranges as named locations and designate them as ‘known,’ further refining the risk assessment process.
- Promptly update location definitions if your office networks or VPN configurations change, ensuring that risk modeling remains accurate and up-to-date.
- Verify location mappings by reviewing sign-in logs to ensure that IP addresses are correctly matching the defined trusted and known locations.
- Exclude unnamed or unknown locations from the trusted or known designations, ensuring that sign-ins from these sources are subject to heightened scrutiny.
- Periodically review sign-in logs to validate the accuracy of your location mappings, making adjustments as necessary to maintain optimal risk modeling.
6. Enable Comprehensive Security Monitoring
Ongoing monitoring and alerting are critical components of an effective risk management strategy. By enabling robust monitoring and integrating Azure Identity Protection with your existing security infrastructure, you can ensure that risk visibility and response coordination become a 24/7 capability, maximizing the value derived from the solution.
To achieve comprehensive security monitoring, consider the following recommendations:
- Configure email notifications for new risky users, risky sign-ins, and weekly digest reports, ensuring that appropriate security team members are promptly alerted.
- Establish a routine for regularly reviewing Azure Identity Protection reports, such as risky users, risky sign-ins, and risk detections, enabling proactive identification and mitigation of potential threats.
- Create Azure Monitor dashboards to visualize risk trends, policy actions taken, and track the status of remediation efforts, providing a centralized view of your organization’s security posture.
- Leverage the Azure Identity Protection workbook template to gain deeper insights through interactive reports, enabling data-driven decision-making and enhanced situational awareness.
- Export Azure Identity Protection events via the Graph Security API to your SIEM solution, enabling correlation with other security-related events for a holistic view of potential threats.
- Within your SIEM solution, correlate risk detections from Azure Identity Protection with other identity-related security events, enhancing monitoring coverage and enabling more comprehensive threat detection.
- Configure automated response workflows or playbooks in solutions like Azure Sentinel, triggering predefined actions based on Azure Identity Protection alerts, streamlining incident response processes.
- Document investigation and remediation processes for security operations teams, ensuring consistent and efficient handling of security incidents.
7. Foster a Security-Conscious Culture through End-User Training
An educated and security-conscious user base is less prone to lapses that can jeopardize account security. Continuous training and engagement initiatives help sustain user cooperation, which is crucial for the successful adoption and ongoing effectiveness of Azure Identity Protection.
To cultivate a security-conscious culture within your organization, consider the following best practices:
- Inform users about new Azure Identity Protection policies, such as MFA registration and risk-based sign-in challenges, explaining the rationale and benefits behind these measures.
- Provide clear instructions and guidance on enrolling for MFA during sign-in prompts, ensuring a smooth user experience and minimizing potential frustrations.
- Train users on proper password hygiene practices, including the use of strong passwords, password managers, and the importance of avoiding password reuse across multiple sites or services.
- Implement self-service password reset (SSPR) capabilities for user accounts, empowering users to maintain control over their account security while reducing the administrative burden on IT teams.
- Raise awareness about phishing attacks and social engineering tactics, equipping users with the knowledge to identify suspicious emails, links, or other potential threats.
- Encourage users to report any suspicious activity, such as unfamiliar sign-in locations or unauthorized access attempts, fostering a collaborative approach to security.
- Incentivize and reward security-conscious behavior among employees, driving engagement and reinforcing the importance of cybersecurity best practices.
- Track training completion rates and measure security awareness over time through simulated phishing campaigns or red teaming exercises, identifying areas for improvement and tailoring future training initiatives accordingly.
8. Leverage Third-Party Solutions
By leveraging the combined power of Azure Identity Protection and advanced solutions like Apono, organizations can establish a comprehensive, identity-centric security strategy that proactively identifies vulnerabilities, mitigates risks, and ensures the protection of their most valuable assets–their identities.
Conclusion
In the ever-evolving cybersecurity landscape, securing your organization’s identities is a critical imperative. Azure Identity Protection emerges as a powerful ally, offering intelligent capabilities to identify vulnerabilities, remediate risks, and enforce access controls. By following the best practices outlined in this comprehensive guide, you can unlock the full potential of Azure Identity Protection, fortifying your defenses and safeguarding your users’ identities from malicious actors.
Remember, a robust security strategy is not a one-time endeavor; it requires continuous vigilance, adaptation, and a commitment to staying ahead of emerging threats. By leveraging solutions like Azure Identity Protection and complementing them with advanced identity threat protection platforms, you can establish a comprehensive, identity-centric security posture that empowers your organization to thrive in the digital age.
Apono and Azure Identity Protection
At its core, Azure Identity Protection leverages machine learning and advanced analytics to detect suspicious activities and potential security threats in real-time. Now, add Apono to the mix, and you’ve got a dynamic duo that ensures your identity management system is not just reactive but proactively securing your digital landscape. Apono enhances Azure’s already powerful suite by offering seamless access governance and compliance tracking, making sure that only the right people have access to the right resources at the right time.
It starts with Apono’s ability to automate access requests and approvals through Azure’s identity management framework. This automation drastically reduces the manual effort needed to manage user permissions, ensuring that your IT team can focus on strategic initiatives rather than getting bogged down in administrative tasks. The synergy between Apono and Azure Identity Protection means that any anomalies or risks identified by Azure are swiftly acted upon by Apono’s intelligent system, which can automatically revoke or adjust access permissions as needed.
Another aspect of this integration is the enhanced user experience. By leveraging Azure’s Single Sign-On (SSO) capabilities, Apono ensures that users have quick and secure access to the applications they need without juggling multiple credentials. This not only boosts productivity but also reduces the risk of password-related security breaches. Furthermore, with Apono’s self-service portal, users can request access or report issues directly, streamlining processes and reducing the workload on IT support teams.
In summary, the collaboration between Apono and Azure Identity Protection creates a formidable defense against cyber threats while optimizing identity management processes. This integration brings together automation, real-time threat detection, comprehensive reporting, and an enhanced user experience to deliver unparalleled security and efficiency. So, if you’re looking to take your organization’s identity protection to the next level, integrating Apono with Azure Identity Protection is undoubtedly the way to go.


