Apono Blog
Healthcare Cybersecurity: Preventing Data Breaches
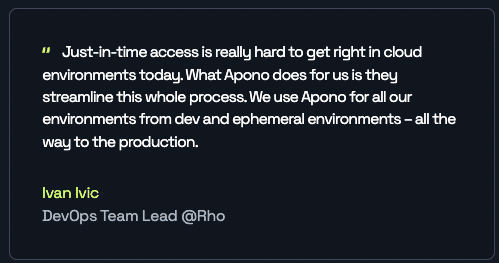
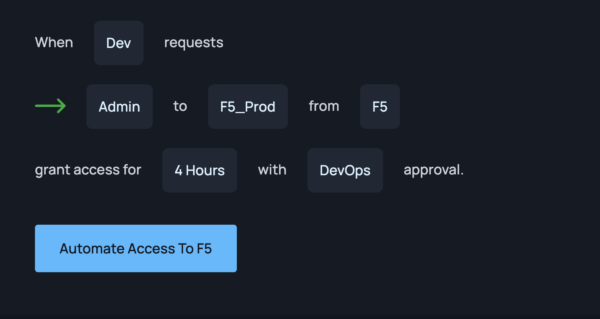
Healthcare organizations find themselves today at the forefront of a disturbing trend: a seemingly unending onslaught of data breaches. These nefarious incidents, far from being isolated occurrences, have emerged as a persistent and pervasive threat, one that demands immediate and comprehensive action to safeguard patient privacy and operational integrity. Understanding the Magnitude of Healthcare Data […]